Flow: Decryption
The decryption node converts the cipher-text into plain text using AWS - Key Management Service (KMS).
Figure below shows the decryption node. The node specific configuration is accessed by double-clicking on the node.

Figure 1: Node
SETTINGS
The key values to be extracted / translated from the input data set and the corresponding output is configured using these settings.
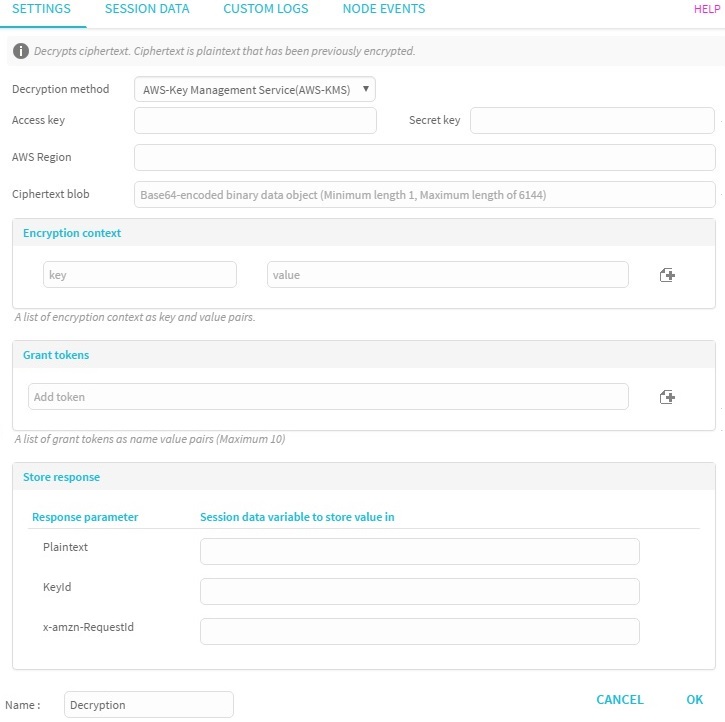
Figure 2: Settings
The table below describes the configuration settings.
Field | Description |
|---|---|
Decryption method | Specifies the decryption method, which is the AWS - Key management service. |
Access key | User identity generated at client-side, enables the client to have their own Access key. |
Secret key | It is generated along with the Access key - for each user account a secret key is generated. |
AWS Region | User's must set the region to the one where the master key is/was generated. |
Ciphertext blob | Ciphertext to be decrypted. |
Encryption context | If the following values were specified in the encrypt function, it must be specified here or the decryption operation will fail:
|
Grant tokens | Contains information about who the grant is for and, who can use it. It is a list of grant tokens as name value pairs (maximum of 10).
|
Store response | Response variables that include the following values that are received in response:
|
SESSION DATA
For information on session data, click here.
CUSTOM LOGS
For information on custom logs, click here.
NODE EVENTS
Node events lists all outcomes of this node. You can add custom labels or terminate (end) an event by setting the termination reason.
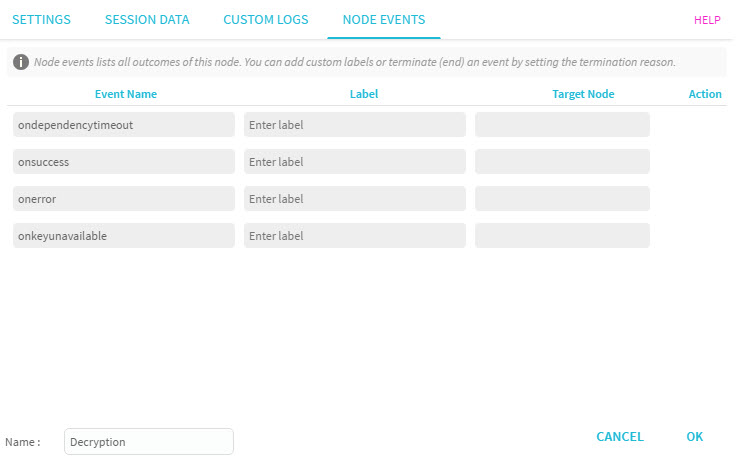
Figure 3: Node Events
Configuration Settings.
Exit Events | Description |
|---|---|
ondependencytimeout | The system timed out while trying to fulfill the request. The request can be retried. |
onsuccess | Input data is successfully decrypted with the value stored in the set parameter. |
onerror | The following errors may have occured:
|
| onkeyunavailable | The request was rejected because the specified CMK was not available. The request can be retried. |
Updated almost 3 years ago